In today’s evolving cyber threat landscape, organizations must be proactive and vigilant in their security measures. Breach and Attack Simulation (BAS) is an innovative approach that automates the simulation of full attack lifecycles against an organization’s infrastructure. BAS solutions help identify vulnerabilities, prioritize remediation, and enhance threat detection and mitigation. With real-time reporting and actionable insights, security teams can make informed decisions and adopt a threat-centric approach. BAS is now an essential component of modern enterprise security, keeping organizations ahead of cyber threats.
What Is Breach and Attack Simulation (BAS)?
Breach and Attack Simulation (BAS) is a proactive security assessment approach that evaluates an organization’s security posture by simulating real-world cyber-attacks. It complements traditional assessment methods and provides a comprehensive evaluation of security. BAS solutions simulate various attack vectors, helping identify vulnerabilities and weaknesses before they can be exploited. Detailed reports generated from these simulations highlight areas of effective control as well as security gaps, enabling organizations to prioritize remediation based on risk level. BAS enhances security measures and strengthens defenses against sophisticated attackers.
A BAS solution helps organizations:
- Prioritize security investments
- Mitigate potential risks
- Minimize the likelihood of successful cyberattacks
As the cyber threat landscape evolves, BAS has become a crucial component of a comprehensive cybersecurity strategy. It ensures organizations stay ahead of attackers and maintain a robust defense against potential breaches.
How Does a Breach and Attack Simulation (BAS) Work?
Breach and Attack Simulation (BAS) mimics the tactics, techniques, and procedures (TTPs) employed by cybercriminals to evaluate an organization’s security controls and identify vulnerabilities.
The BAS process starts by selecting a scenario, which can be based on:
- Emerging threats
- Custom-defined situations
- Known attack patterns observed in the wild
- Advanced Persistent Threat (APT) groups that target specific industries.
During the simulation, the BAS platform continuously monitors the organization’s security controls, such as: firewalls, IDS/IPS systems, anti-virus, anti-malware, endpoint protection, Data Leak Prevention (DLP), Security Incident & Event Management (SIEM) solutions, to evaluate their effectiveness in detecting, preventing and mitigating simulated attacks. The platform also collects valuable data on the attack’s progress, providing the organization with insights into the potential risks and gaps in their security posture.
After the simulation, the BAS platform generates a detailed report that includes discovered vulnerabilities, security control performance, and recommended remediation measures. This information helps organizations prioritize security enhancements and enhance protection against real cyber threats. BAS provides a safe and controlled environment for cybersecurity testing that allows organizations to identify and address vulnerabilities before actual attackers exploit them, thereby improving their overall security.
Picus Complete Security Control Validation Platform
The Picus Complete Security Control Validation Platform is a Breach and Attack Simulation (BAS) solution that automatically validates, measures, and helps enhance cyber resilience 24/7. With this comprehensive and easy-to-use solution, security teams can quickly:
- Measure and optimize the protection provided by existing security controls
- Discover and eliminate attack paths to critical systems and users
- Optimize detection and response capabilities to eliminate attacks sooner
The Picus Platform provides the capability needed to assess the organization’s security posture automatically, continuously, and consistently while optimizing defenses 24×7.
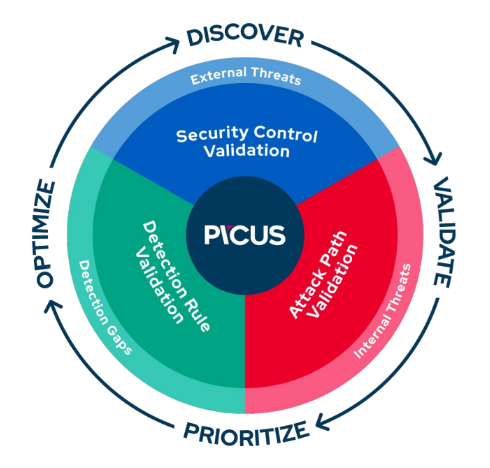
Security Control Validation:
Simulates real-world cyber threats to validate and enhance the effectiveness of security controls to prevent and detect attacks. Security validation is performed for both prevention controls and detection controls.
- Prevention control validation: Picus automatically validates the effectiveness of firewalls, antiviruses, Data loss prevention, intrusion prevention systems, among others. This is done by simulating different types of threats such as Malware Attacks, Email attacks, vulnerability exploitation attacks. These attacks come from the extensive Picus Threats Library which contains over 3800 threats and is updated daily by Picus’ team of experts.
- Detection control validation: The Picus platform also helps ensure that detection controls remain effective by obtaining telemetry data in real time and suggesting actionable insights that will aid in achieving optimal protection. Picus can integrate with both Security Incident and Event Management systems (SIEM)and Endpoint Detection and response systems (EDR).
SIEM Partners:

EDR Partners:

Attack Path Validation: Discovers and helps eliminate high-risk attack paths to critical systems and users in internal networks.
Detection Rule Validation: Optimizes detection and response by identifying issues related to the performance and hygiene of detection rules.
The Picus Platform offers a comprehensive approach by validating multiple aspects of cybersecurity, allowing for a tailored solution that aligns perfectly with specific requirements. Their commitment to simplicity ensures that the security validation process remains quick and easy, eliminating complexity for every organization. What sets Picus apart is their outcome-focused approach. They not only identify security risks but also provide the tools and support necessary to address them swiftly and effectively by making changes to configurations, adjusting blocking parameters, and changing SIEM rules. With Picus, you can proactively protect your organization and achieve robust security outcomes.
Summary
At MAKINSIGHTS we leverage the Picus platform in our Immediate Threat Analysis Service (ITAS) which aims not only to provide all the protections and enhancement capabilities of the platform but also guidance for Board Member and Executives about cybersecurity strategy and investments.
If you want to know more about how ITAS and the Picus platform can take your cyber security capabilities to the next level contact us at ideas@makinsights.com or through calendly HERE.
Sources:
https://www.picussecurity.com/resource/glossary/what-is-breach-and-attack-simulation
https://www.picussecurity.com/hubfs/Datasheets%202023-%20latest%20versions/Picus-Prevention-Controls-Datasheet-2023.pdf?hsCtaTracking=9e09b7c5-b5da-4b2e-a18e-a69d6e48b772%7C90d99dda-2877-46cd-8f17-26366cd637a3
Schedule a complementary conversation now!
Implementing FAIR's ontology perspective is a proactive step towards building a resilient and secure digital ecosystem.
Contact us
