Harnessing Breach and Attack Simulation for Cyber Resiliency
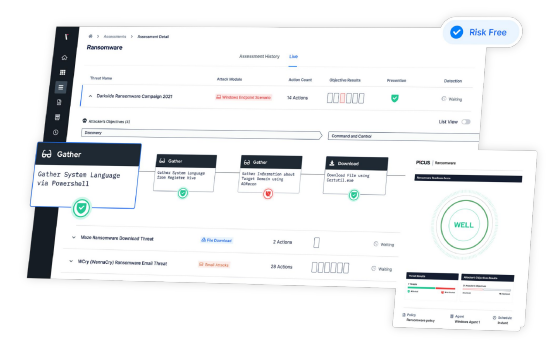
In today’s rapidly evolving digital landscape, enterprises across all verticals face a myriad of distinct cybersecurity challenges. For verticals such as Manufacturing, Healthcare and other Critical Industries that have significant technical debt coupled with limited funds/resourcing, it can be incredibly complex to safeguard assets from Ransomware and other cyber-attacks due to the constant change and …
Harnessing Breach and Attack Simulation for Cyber Resiliency Read More »